Is it safe to store data in a
US-based Cloud provider?
Is it possible to use the cloud securely? What is the Cloud Act and can encryption keep personal data safe from US authorities?
What makes the cloud so attractive? In a nutshell: convenience. It saves money on IT resources, it's more accessible, no need to maintain servers, and it facilitates collaboration within your organization - in short: there are many advantages to working with the cloud. However, after Schrems II ruled the Privacy Shield agreement obsolete, many feel uncertain about using the cloud.
The main reason for the Shrems II ruling was the US CLOUD Act. This allows US authorities to access data stored in US-based cloud services. This is in direct conflict with the GDPR, which exists to protect the privacy of European citizens. The Privacy Shield was not adequate in upholding the GDPR.
Security should be a first priority for all organizations. But there is no denying that Schrems II also slowed down digitization for many European organizations. Many big cloud clients are US-based, after all. As a result, new questions have been raised: Is it possible to use the cloud safely? What is the Cloud Act and can encrypted data protection keep personal data safe from US authorities? This whitepaper helps you navigate those questions.
This whitepaper discusses the CLOUD Act, the Schrems rulings, the Privacy Shield, and their impact on data security in Europe. Is it possible to use the cloud securely? How can encryption aid data security in the cloud? This whitepaper aims to answer all of these questions and more.
A tale of the cloud
What is Schrems II? How does the Cloud Act affect data storage in the cloud? What happens now that Privacy Shield is no longer a sufficient basis for to comply with data protection requirements? Is the cloud still safe to use? In order to answer these questions, let's start at the beginning: Schrems I.
The lawsuit that started it all... Schrems I
.webp?width=752&height=504&name=Max%20Schrems%20Bron%20The%20Irish%20Times%20(1).webp)
Max Schrems. Bron: The Irish Times
It all started with Austrian lawyer and activist: Maximilian Schrems, who had long been wary of Facebook. Although Facebook is an American company, their European headquarters are located in Ireland. European data was therefore freely transferred between Ireland and the US. Schrems, uncomfortable with this free-for-all transfer of his data, filed a claim with the Irish Data Protection Authority in 2013. The claim was filed to prevent Facebook from proceeding with the data transfer of European data to the US.
This came as no surprise. Earlier that year, whistleblower Edward Snowden had proved that Facebook was involved in the controversial PRISM mass surveillance program. Schrems argued in his complaint that this mass surveillance system violated EU data laws.
The case became a high-profile case and went all the way up to the European Court of Justice. Schrems reigned victorious. The Safe Harbor agreement, which had been used until then for transatlantic data transfers, didn't provide a high enough level of protection for data to continue to be shared in this way. The ruling came to be known as Schrems I after the Austrian lawyer, and snip snip snip, that part of the story was over.
Schrems II: Privacy Shield and the Cloud Act
What's a story without its sequel? Schrems I was quickly followed up by Schrems II: The Return. Schrems I ended when the Safe Harbor agreement was repealed. In its place the Privacy Shield trade agreement came into existence. The Privacy Shield served as a framework that allowed European and American companies to exchange data while meeting certain privacy requirements.
The European Commission had previously decided that the Privacy Shield provided an adequate level of protection for processing personal data. However, that decision was struck down in the summer of 2020 when Schrems filed another complaint. He argued that the Privacy Shield was not a better alternative than the Safe Harbor.
The court ruled once more in Schrems' favor. The reason? The US CLOUD Act, introduced in 2018. This Act allows US authorities to request European data stored with US cloud providers, which goes directly against the GDPR. The Privacy Shield, too, was struck down.
This judgment was then called C-311/18, but is better known as Schrems II... Although we personally think that Schrems II: The Return would have had a slightly more dramatic ring to it.
%20(1).webp?width=451&height=359&name=gavel3%20(2)%20(1).webp)
The consequences?
Schrems II slowed down digitization for organizations that had already moved to the cloud or were planning to do so. After all, clouds were beholden to the US CLOUD Act and possible data requests from US authorities. The biggest question was centered around whether it was possible to be GDPR-compliant in the cloud or whether it's time to find an alternative for storing our data.
What does the European Data Protection Board say?
With all this in mind, what does the GDPR actually say about storing data in third country or with a US cloud provider? The European Data Protection Board (EDPB) has set out a number of criteria for what this should look like:
1. Personal data must be encrypted before being sent.
2. The encryption algorithm used must be of a high standard and robust enough to withstand encryption analysis by authorities in the recipient country.
3. The strength of the encryption must consider the length of time during which the confidentiality of the encrypted data is to be maintained.
4. The encryption algorithm must be implemented flawlessly by regularly maintained software and verified by, for example, certification.
5. The encryption keys must be stored in a reliable way.
6. Only the data exporter and authorized recipients may have access to the encryption keys. They must be located within the EEA or in a third country where an adequate level of protection is maintained, as required by Article 45 of the GDPR.
.webp)
Perfect – clear and concise
So how do we approach these rules? The answer, as the EDPB mentions, lies in the encryption and management of encryption keys.
Does data encryption protect against the CLOUD Act?
Encryption is a requirement for secure communications. Why? Without encryption, your information is open to view for anyone. View it like leaving your front door unlocked: anyone with ill intent can break in and take a gander at your inventory. Email works similarly.
The purpose of encryption is to encode your information in such a way that only authorized people can access it. It sounds simple enough. But it is more complex than that, there are many different types of encryption. Some will only protect you from hackers, but not the US authorities. In order to comply with the GDPR, it is important that your data protection uses encryption that protects against the CLOUD Act.
Cloud Act
The CLOUD Act gives US authorities the right to access your data if you use a cloud provider based in the US. This applies regardless of where the data is currently stored. If your cloud provider is a US-based company, it doesn't matter if your data is stored in Europe. Therefore, to protect yourself against the CLOUD Act, you need data protection that uses zero knowledge encryption.
Zero Knowledge
Zero knowledge means that no one, except for the sender and recipient, have access to the encryption keys to decode your data. And no, neither does your encryption provider.
It's important to note that zero-knowledge encryption does not prevent a third party from accessing your data. But it does prevent them from accessing this information in a meaningful way: they can only view the encrypted data. The decrypted data can only be read by the sender and the recipient because they hold the key to unlock the data.
To summarize: with zero knowledge encryption, US authorities can still access your information, but they can't read it. Smart, right?
Does encrypted data protection therefore protect against the CLOUD Act?
We let GDPR and data security expert Alexander Hanff sum it up.
"Absolutely, from the perspective that it (data protection) makes the data unreadable or useless."
How to comply and protect your data? With data and security expert, Alexander Hanff
Does Schrems II mean that organizations are violating the GDPR? What can you store in the cloud? Is it possible to get the best of both worlds: the benefits of cloud solutions and adequate information security?
Get answers to all these questions with our webinar!
What should I consider when choosing encrypted data protection?
That was a lot of information! Let's take stock: the cloud offers a simplified, cheaper and smoother way to work, but it must comply with the GDPR. That's why you need encrypted data protection. So when you're ready to choose an encryption provider, please consider the following:
Awareness
Just how experienced is your provider? Ask them how they manage their encryption keys. What type of encryption do they use? Are they aware of any future risks associated with this type of encryption? Do they regularly update their solution?Storage of encryption keys
Your provider should use end-to-end encryption with zero knowledge. This is non-negotiable. By using zero knowledge end-to-end encryption, no one, except for authorized people, can access your data in a meaningful way. This way you are both GDPR-compliant and protected from the CLOUD Act.
%20(5)%20(1).webp?width=400&height=440&name=cybersecurity%20(1)%20(5)%20(1).webp)
Smartlockr and encryption
Last, but certainly not least, we have arrived at Smartlockr. How do we manage your data? Smartlockr's secure email solution uses end-to-end encryption with zero knowledge.
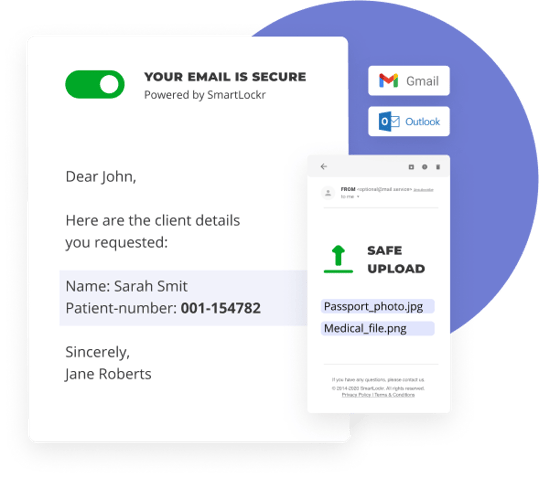
End-to-end encryption
By sending secure email with Smartlockr, we ensure that the entire email is encrypted: both the message and any attachments you may send. This applies throughout the entire process.
In the past, the focus was usually on securing the connection between the sender and the recipient to ensure security. Unfortunately, this meant that if someone gained access to the email during sending, there was a high risk that the information in the message could be exposed.
End-to-end encryption means that the entire message is encrypted before, during and after you send it.
Zero knowledge
As previously discussed, zero knowledge means that the encryption keys are stored separately from the provider. Only authorized recipients have access to the keys. If a third party were to gain access to your email or an attachment, the information is not useful to them as it will be encrypted and thus unreadable.
- Comply with local laws and regulations: Such as GDPR and SDK;
- User-friendliness first, so that security will actually be used;
- Increase awareness and make your own people your best protection against data breaches;
- Fully integrates into your work process, your email environment and mobile phone, with no extra hassle. That way it's easy to use for everyone;
- Keep control of your data. Track and block your email, recipient(s) and/or attachment(s) as needed.

